buuctf7
[安洵杯 2019]easy_web
看到img的后面像base64,解密两次后再经过hex解密,得到一个文件名称,于是尝试读取index.php源码,
hex->base64->base64
抓包在cmd上做手脚,发现传入数组类型的时候,有回显array,这个时候总觉得有点函数嵌套那味了
1 | <?php |
又是md5的事情,直接进了
md5碰撞:
1 | a=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2&b=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2&= |
在linux系统中:
1 | cat /flag |
[网鼎杯 2020 朱雀组]phpweb
页面一直在刷新,路径也知道了,先抓个包看看,发现可以提交表单,然后用了call_user_func这个危险函数:
call_user_func — 把第一个参数作为回调函数调用
使用file_get_contents查看index.php源码
1 | <?php |
果然在一条路上卡太久应该积极转化思路,当我苦苦搜素手册无果的时候,最终选择打开了wp,原来可以利用反序列化来解题:
1 |
|
这里有一点需要说明的是,eval不是函数所以这里的call_user_func就不适用了,所以选择system来构造payload,不过这个拿到flag的语句也是让我眼前一亮
[De1CTF 2019]SSRF Me
1 | #! /usr/bin/env python |
python代码审计:
在python2.7中跑,想说用debug了解一下整个代码的运行逻辑,但是跳来跳去的,实在看不明白,可能是由于都是由def的函数形式,所以打算去看看如何审计此类代码:
大概进程就是如上所示,接下来要考虑的就是漏洞在哪里,思路都写在上面了,现在传值看看:没有反应,密钥都没有我传个鬼–,学习了路由的知识后,发现其实不止index.php一个入口还有geneSign 还有De1ta入口,这里
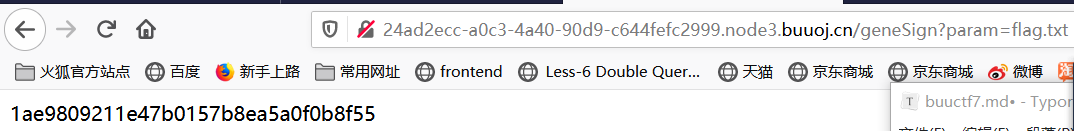
根据提示,传入flag.txt查看到密钥
1 | 1ae9809211e47b0157b8ea5a0f0b8f55 |
(这里不是很懂为啥能查看到密钥?也没有相关代码呀,是我看得不够仔细吗),被wp给误导了,其实也不算误导,应该是我理解错了
这里重新理一下思路:其实这里主要绕过的就是一个checksign函数和一个waf函数
check函数需要比对的内容是将param和action以及密钥进行拼接,再与我们传入的sign进行比对,但是问题在于,我们没有密钥,所以解题的关键就在这里,我们知道flag在flag.txt文件中,而在genesign中 如果我们传入flag.txt那么返回的内容即为
secret_key+flag.txtscan的md5加密,但是后面的action只能是scan会不会有影响呢?其实不会的,因为这也是我们所需要的,进入到exec函数中,其实有两个判断,一个是read一个是scan,当我们在scan前加上read,那么判断就会进入read当中,即可使用read()函数打开flag.txt了
救命,终于有不一样的回显了!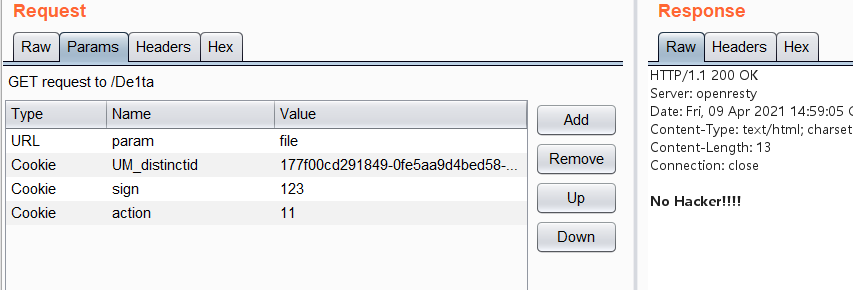
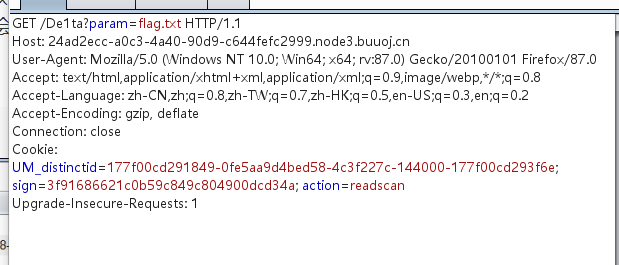 最终payload
最终payload